Successful businesses rely on a variety of ecosystems of trusted partners, such as suppliers and resellers, to create compelling offers to their end customers. These ecosystems often have established eligibility criteria and compliance requirements that each partner has to fulfil to become ‘part of the game’. As an example, if a vendor of automotive parts wants to be listed as an official supplier to a car manufacturer, it not only has to pass quality assurance for its parts, it also has to comply with other requirements, such as standards regarding governance and sustainability. Conversely, if a consumer buys a new car, he or she relies on the car manufacturer having carefully selected quality parts, fitted the parts correctly and built the car according to current standards.
Now, what does the situation look like in the digital age? If, for example, a digital enterprise sells its goods online, it has most likely already implemented a multi-channel strategy, offering these goods both via its own web presence and via a broad variety of online marketplaces and partner sites. It is working with partners such as content delivery networks to optimise web performance and gain insight into customer behaviour. Changing perspective, the consumer not only needs to trust the enterprise and the quality of its goods – he or she also needs to trust the whole chain of digital communication and the respective partners involved.
Thus, the digital enterprise has to establish a digital ‘trust chain’ that guarantees the integrity of its digital assets offered over a variety of different communication infrastructures and partners involved.
There are also trust chains for ‘internal’ applications of the digital enterprise: employees will need to use a variety of applications – some hosted internally, some in a public cloud, others as applications sourced externally as SaaS, perhaps on a variety of devices. The application user will certainly ask for ‘single sign-on’, i.e., the possibility to authenticate only once and then get access to all ‘internal’ systems – in other words, a trust chain of access to internal applications is needed even if these applications are SaaS applications from a third party hosted in some cloud. Identities must be shared between applications for user convenience reasons, as well as propagated down the application processing chains.
So, what are the basic principles for implementing a digital trust chain? In another section, the concept of digital identity as a fundamental tenet of digital trust has already been introduced.
Moving to the underlying technical key concept here, we need to understand that…
in order to implement digital trust chains, the so-called ‘federation of identities’ is required.
According to Gartner, ‘Federated identity management (FiM) enables identity information to be developed and shared among several entities and across trust domains.’
It is important to note that this is not a new concept per se in the digital age. However, over the past decade many attempts to implement on-premise FIM in a scalable manner have illustrated the complexity of the challenge. To understand this, take a closer look at a potential implementation of the proposed single sign-on for employees described above:
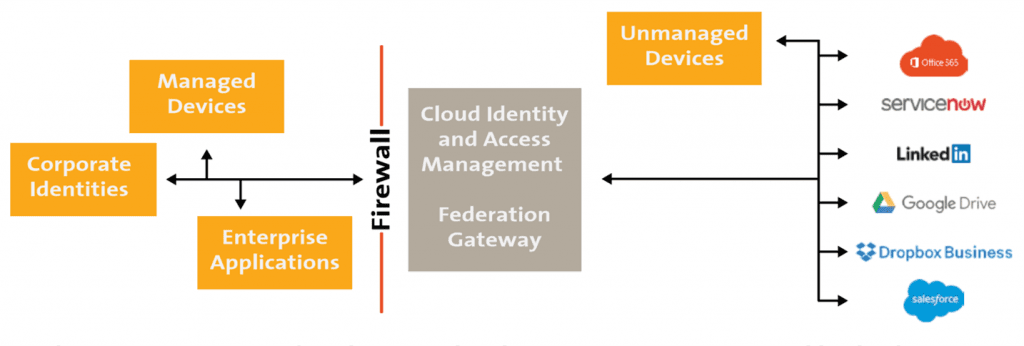
Employees want to access a broad variety of applications – on-premise, in a public cloud, via SaaS –with only one authentication process, while possibly each of these applications will ask for a different kind of authentication token.
So, essentially, a federation gateway must be implemented that handles the core work of translating the one given preferential token of the user into all other formats needed.
And with every new application may come the need for a new token.
Interestingly, new cloud-based security services can lead the way out of this challenge: Cloud Identity and Access Management (CIAM) systems[1] implement a federation gateway in the cloud, federate the on-premise identity only once and then take on the complex burden of leveraging this single copy to all other cloud services. In other words, they ensure ‘who’ is using the application.
A good example of this is the ‘social login’, where a consumer can log into a new social website by, for example, using their Facebook or Google credentials. In a similar way, so-called Cloud Access Security Brokers (CASBs)[2] can help us overcome the challenges of visibility, data security, threat protection and ensuring compliance once we start running our applications in the cloud.
Summing up, we have a solution strategy that would work in the digital context: build trust chains based on the federation of identities implemented via trusted CIAMs and CASBs encrypting all data and traffic where applicable. However, we must be aware that challenges do remain in this area. Digital enterprises and their customers need to:
- Choose the right partners and live with their potential risks (for example, ‘Cloudbleed’ or the Amazon S3 outage).
- Trust the relevant state-of-the art technologies, which are often challenged by reality (consider NSA RSA ‘crack’ backdoor or NSA Diffie-Hellman).
- Trust in their digital ecosystem (think about Wikileaks Vault 7).
For long-term success, it is mandatory that the digital enterprise continually monitors and evaluates each trust chain of which it is a part, in order to be able to react to challenges as soon as possible.
The enterprise can outsource such analysis to security specialists that can relatively easily build up the critical security-relevant intelligence and analytical capabilities. Fighting cybercrime and avoiding internal security weaknesses are becoming core capabilities that every digital enterprise must master.
_____
[1] Mahmood, Z.: ‘Continued Rise of the Cloud: Advances and Trends in Cloud Computing’, Springer, p. 92, 2014
[2] Vacca, J. R.: ‘Cloud Computing Security: Foundations and Challenges’, Apple Academic Press Inc., p. 430, 2014.