Digitalisation has dramatically broadened both the surface of attack and the potential means of an attack: most of today’s physical assets, such as TVs, cars or even nuclear plants, already have digital components or functions and can thus be both the target or part of a digital attack. Examples include the famous Stuxnet[1] worm that targeted the programmable logic controllers of Iranian centrifuges to finally sabotage Iran´s nuclear programme. The IoT adds a new dimension: on 21 October 2016, a massive Internet attack was launched via hacked IoT devices like closed-circuit video cameras and digital video recorders.[2]
It is certainly fair to say that, in the digital age, IT security needs to be at the centre of the enterprise’s overall security strategy.
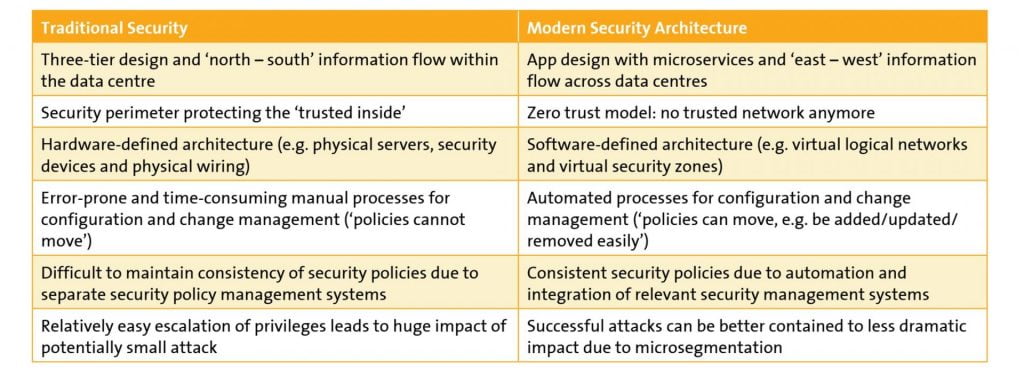
In addition, digitalisation has a dramatic impact on the guiding principles of how we design and build IT applications and the structure of their interaction. This, in turn, completely changes the way we need to think about IT security. Today, modern applications are designed to consist of hundreds of microservices, which are often shared across data centres – and are used by many applications. This creates a lot of necessary and legitimate ‘inter-services’ network traffic, which completely undermines the good old principle of a security perimeter separating the ‘untrusted outside’ from the ‘trusted inside’. Data centre infrastructure could be private, hybrid or public cloud, and applications are no longer monolithic stacks, but truly distributed systems, using shared services such as Domain Name Services (DNS), mobile applications or software as a service.
It is obvious that the old paradigm of a trusted internal and an untrusted external network is meaningless in this context of distributed applications across clouds.
Thus, our security architecture cannot just evolve; instead, we have to completely rethink our security strategy.
So, back to basics: the key goal of information security is to ensure secure interactions of legitimate users and relevant data via applications, in particular their confidentiality, integrity and availability. Historically, most of our security controls have been implemented within the network infrastructure, implementing a security perimeter around our trusted internal network. In our new paradigm for security in the digital world, we need to focus on protecting data and users and their interactions via applications on a physical infrastructure that we cannot control – and hence, we cannot trust.
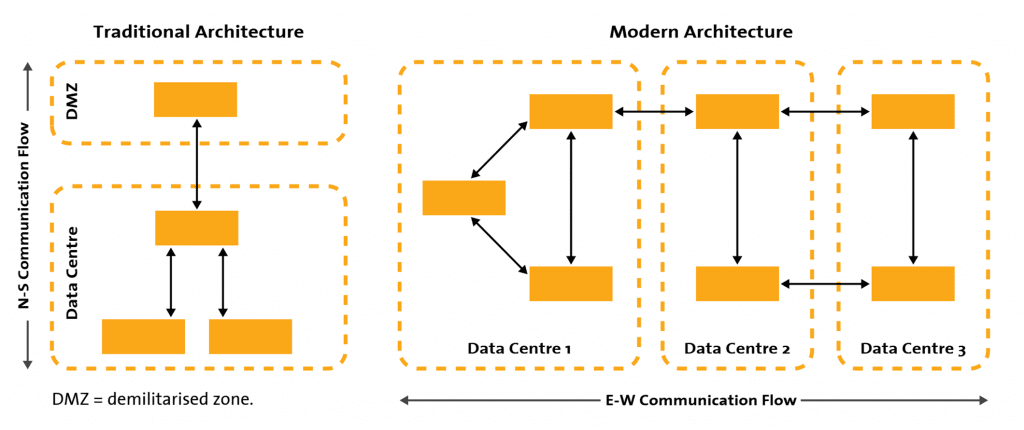
The baseline of our new security strategy is what Forrester calls a ‘Zero Trust Model’[3] with the following three key concepts: ensure all resources are accessed securely regardless of location; adopt a least privilege strategy and strictly enforce access control; and inspect and log all traffic.
Accordingly, our new guiding principles must be:
- Data: ‘Data at rest’ must be strictly classified according to security and compliance impacts and will be protected via access control, inspection of usage, encryption and finally deletion if no longer needed. ‘Data in motion’ are best protected by end-to-end encryption and only legitimate decryption for security purposes. While part of this seems mainly to be just proper use of technology, it is a very complex challenge from a process point of view and also needs involvement of business lines, in particular with respect to the necessary classification of data.
- Users and applications: We need to find ways to align our security controls more closely with the users and the applications and, as a breach may still happen, to minimise the potential impact of the breach. In a world of millions of applications, and at least hundreds of applications within a current enterprise, the guiding principle is an application-centric approach to security.
The new security architecture has to allow for ‘segmentation per application’, with central monitoring of its end-to-end usage and the possibility to centrally define and put into action relevant controls in real time. In addition, we need to take into account that our typical logical infrastructure building blocks will most likely not stay on the same physical device, but will be moved to the most cost-effective hardware resource over time. The security architecture will be distributed in nature allowing for very granular and dynamic security controls.
[show_ad id=”9003241321004368″]
Think of the following analogy in the physical world: instead of just protecting a security zone with firewalls, and putting at risk all the people inside the zone if the fire somehow gets into the protected zone, we equip each person with an individual ‘risk-dependent’ protection suit so that he or she can move around safely even in an ‘untrusted’ dangerous environment.
Today, most of the relevant technology for the new security architecture already exists, but its proper adoption and implementation requires deep organisational transformation, in particular as IT security can no longer be viewed as just a separate task of a separate business unit; it needs to be an integral part of the whole service end to end.
_____
[1] Gaycken, S.: ‘Wer war’s? Und wozu?’, Zeit Online, Vol. 48, 2010.
[2] Thielman, S., Hunt, E.: ‘Cyber attack: hackers “weaponised” everyday devices with malware’, The Guardian, 2016.
[3] Kindervag, J., Balaouras, S., Mak, K., Blackborow, J.: ‘No More Chewy Centers: The Zero Trust Model Of Information Security’, Forrester, 2016.